写在前面
本人是西电计科大二学生,对计算机系统安全较为感兴趣,找到MIT的CS6.858来听,对应课程网站如下:
1 | https://ocw.mit.edu/courses/6-858-computer-systems-security-fall-2014/ |
该文章是结合6.858和自身实际情况,欢迎各位大佬来交流完善
本课程学习方法:
正文
Lecture1 Introduction & Threat Model
Introduction
What is Security? —> Goal VS Adversery,分为以下三方面:
正确的assumption很难与事实相吻合,因为adv的手段都比较出乎意料。
具体例子看对应lec1讲义
Case Study : Buffer overflows
Demo:A sys which has a web server
Threat Model:Assume that adv can connect to web server,supply and inputs
Policy:a bit fuzzy,only perform operations intended by programmer?
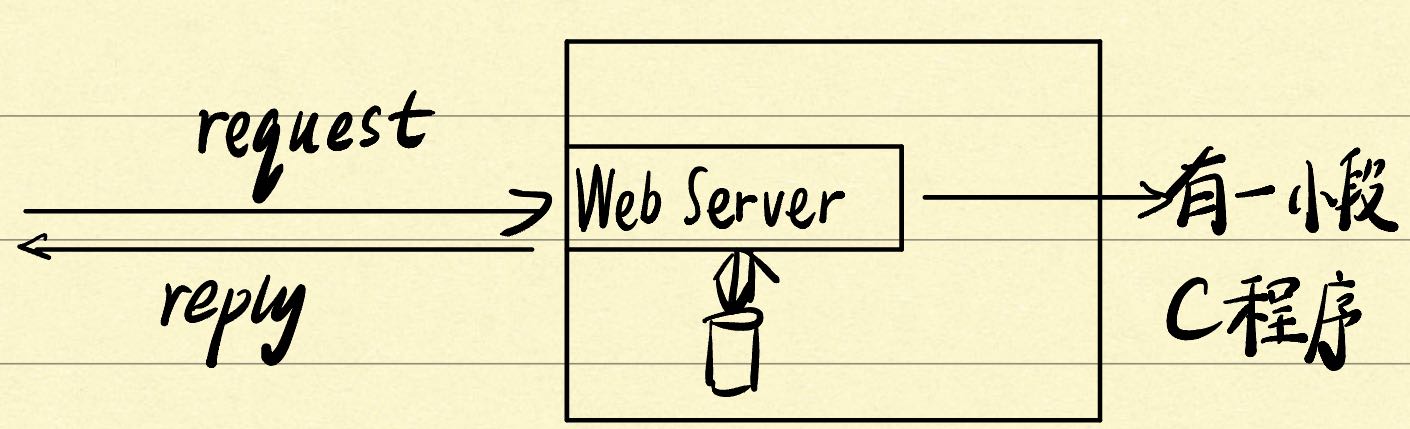
1 | int read_req(void){ |
x86 stack如下:
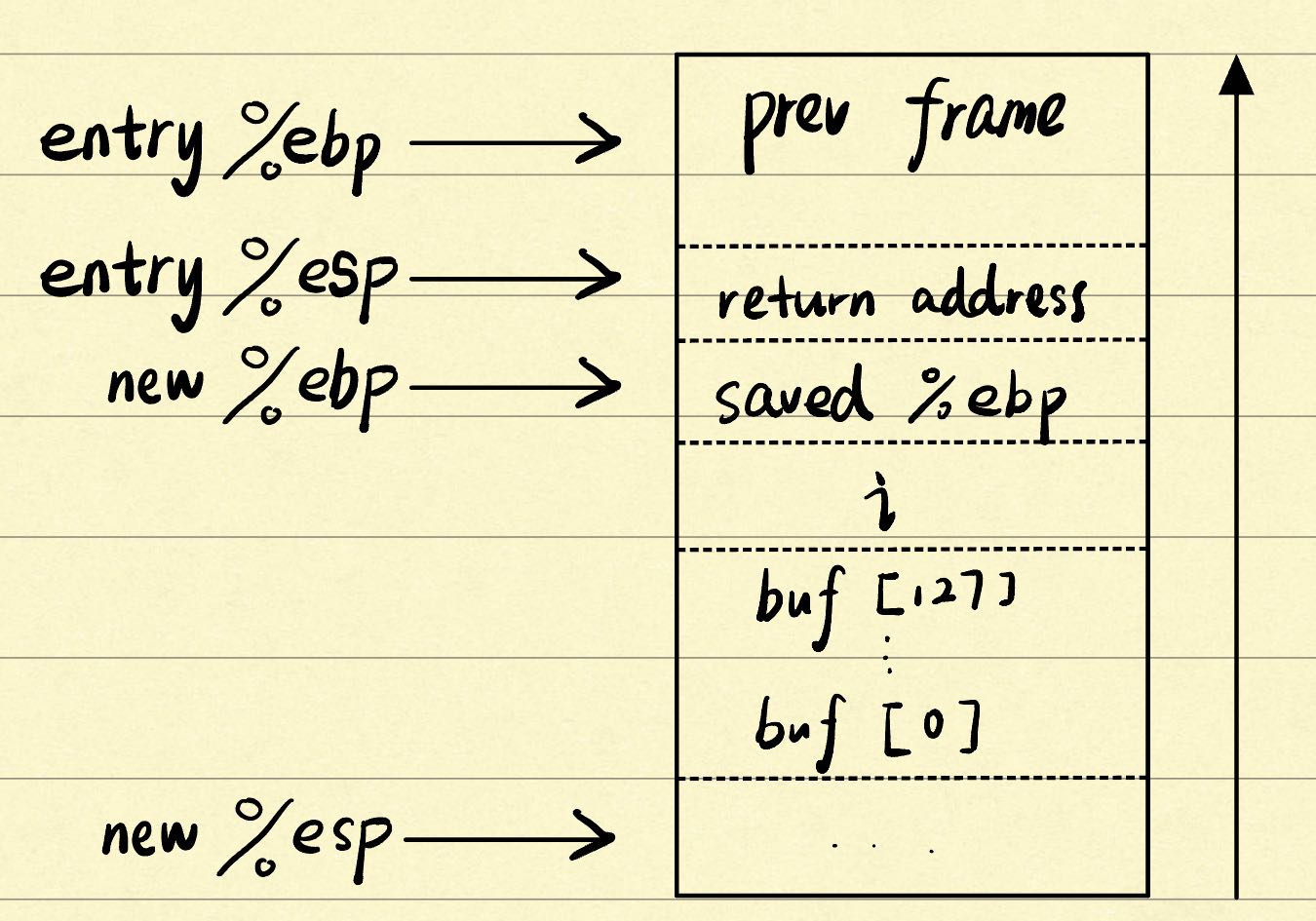
%esp points to the last(bottom-most) valid thing on the stack
esp:栈指针寄存器(extended stack pointer),其内部存放一个指针,该指针永远指向系统栈最上面一个栈帧的栈顶。
%ebp points to the caller’s %esp value
ebp:基址指针寄存器(extended base pointer),其内部存放一个指针,该指针永远指向系统栈最上面一个栈帧的底部,ebp只是存取某时刻的esp。
Why would programmers write such code?
·Legacy code,wasn’t exposed to the Internet
·Programmers were not thinking about security
·Many stdfuncs used to be unsafe(strcpy,gets,sprintf)
·Even safe versions have gotchas(strncpy does not null-terminate)
So,how to avoid mechanism problems?
·Reduce the amount of security-critical code
·Avoid bugs in security-critical code:
-No gets(),use fgets() which can limit buffer length
-Use common,well-tested security mechanisms(Eg:”Economy of mechanism”)
·Examples of common mechanisms:
-OS level access control(后面要讲)
-network firewalls
-cryptography , cryptographic protocols
Lecture2 Review of Buffer Overflow Attacks
栈溢出详解
How does the adv take advantage of this code?
step1.Supply long input, overwrite data on stack past buffer.
step2.Key observation1:attacker can overwrite the return address , make the program jump to a place of the attacker’s choosing!
step3.Key observation2:attacker can set return address to the buffer itself , include some x86 code in there
基本的思路是提供一个恶意的汇编代码去运行,通过覆写栈上的返回地址指向到那个代码。这有点像病毒侵入一个细胞,颠覆它,然后引入一些 RNA 去达到它的目的。
Fixing Buffer Overflows
1.Avoid bugs in C code
1 | strncpy() instead of strcpy() |
2.Build tools to help programmers find bugs
Bad:
Difficult to prove the complete absence of bugs, esp. for unsafe code like C.
Good:
Even partial analysis is useful, since programs should become strictly lessbuggy. For example, baggy bounds checking cannot catch all memory errors, but it can detect many important kinds.
3.Use a memory-safe language (JavaScript,C#,Python)
Good:
Prevents memory corruption errors by not exposing raw memory addresses to the programmer, and by automatically handling garbage collection.
Bad:
Still have a lot of legacy code in unsafe languages (eg:FORTRAN).
Mitigation
Approach 1:canaries(栈金丝雀)

过去煤矿工人下井时会带一只金丝雀,因为金丝雀对煤矿中的瓦斯气体非常敏感,如果进入煤矿后,金丝雀死亡,说明瓦斯超标,矿工会立即撤出煤矿,金丝雀作为煤矿中瓦斯预警器来使用。在 Linux 中我们将 cookie 信息称为 Canary。Canary 与 Windows 下的 GS 保护都是缓解栈溢出攻击的有效手段,它的出现很大程度上增加了栈溢出攻击的难度,并且由于它几乎并不消耗系统资源,所以现在成了 Linux 下保护机制的标配。
原理:函数被调用之后,立即在栈帧中插入一个随机数,函数执行完在返回之前,程序通过检查这个随机数是否改变来判断是否存在栈溢出。
Canary must go “in front of” return address on the stack,so that any overflow which rewrites return address will also rewrite canary.
“in front of”解释:地址在ret address的前一个
The canary must be either hard to guess,or it can be easy to guess but still resilient against buffer overflows.Here are examples of these approaches:
•“Terminator canary”: four bytes(0, CR, LF, -1)
Idea: Many C functions treat these characters as terminators(e.g.,gets(), sprintf()).
As a result, if the canary matches one of these terminators, then further writes won't happen.
• Random canary generated at program init time: Much more common today (but,you need good randomness!).
不能是伪随机数,比如JAVA里面的Random(),是要填入种子的,但是很多人都忽略了这一事实,容易被猜中。
但是栈金丝雀也有不能Catch到的Vulnerabilities,从而实现金丝雀绕过:
Eg:金丝雀泄露
注意:每种方法都有特定的环境要求。
原理:Canary 设计为以字节 \x00 结尾,本意是为了保证 Canary 可以截断字符串。 泄露栈中的 Canary 的思路是覆盖 Canary 的低字节,来打印出剩余的 Canary 部分。 这种利用方式需要存在合适的输出函数,并且可能需要第一溢出泄露 Canary,之后再次溢出控制执行流程。
Approach 2:bounds checking(边界检查)
下面是几种实现方法
1.Electric fences(电子围栏)
Align each heap object with a guard page, and use page tables to ensure that accesses to the guard page cause a fault.
只要引用无效内存地址,立刻故障。

Summary:Electric fences can be useful as debugging technique, and they can prevent some buffer overflows for heap objects. However, electric fences can’t protect the stack, and the memory overhead is too high to use in production systems.
2.Fat pointer(胖指针)
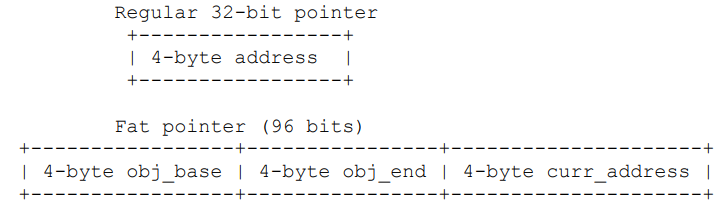
Idea:修改指针本身来查看信息
胖指针也有局限性:
· It can be expensive to check all pointer dereferences. The C community hates things that are expensive, because C is all about SPEED SPEED SPEED.
· Fat pointers are incompatible with a lot of existing software.
Lecture3 Buffer Overflow Exploits and Defenses
对lec2的补充和延申